Proxy server definition
A proxy server is a system or router that provides a gateway between users and the internet. The purpose of a proxy is to prevent cyber attacks and control access to the internet.
Proxy Analogy
Imagine you want to purchase a computer, but instead, you ask someone else to do it and get it for you. Isn’t he a proxy? Indeed, because he’s doing something on your behalf. The same concept applies to computers. If you want to visit www.google.com, your computer will send the request to a proxy server, and the proxy server will fulfill your submission to get back to you.
Types of Proxy Servers
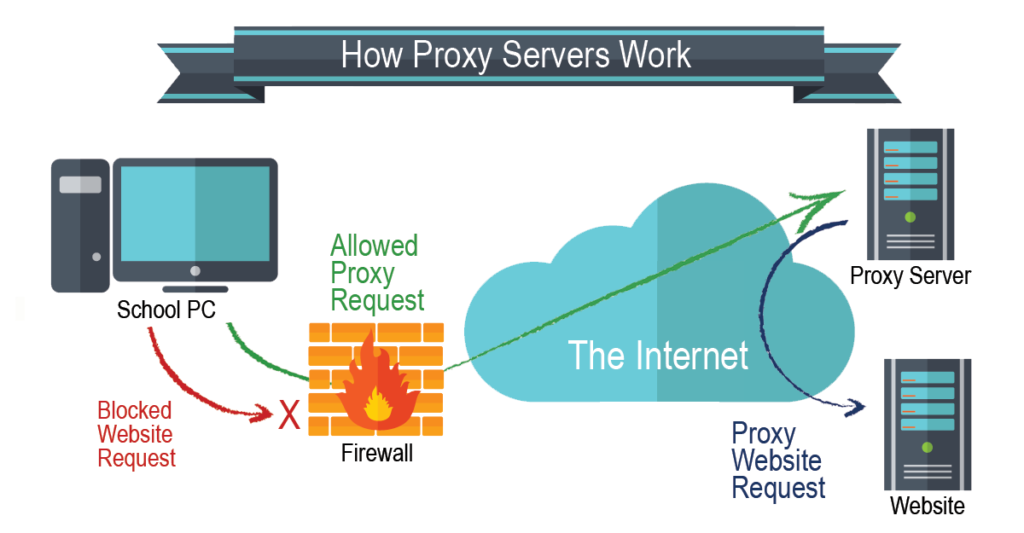
Forward Proxy
A forward proxy sits in front of your network. See the image below. When a client sends a request outside your local network, the proxy server will process it for you. For example, you want to visit www.youtube.com. Instead of your computer linking you directly to the internet, the traffic will be sent to the proxy server. Then, the proxy examines it to decide whether it should proceed to make a connection. This proxy type is best suited for internal networks for a single entry point. The good thing about this is that the server is caching the information rather than passing the request connection to the internet.
Forward Proxy Workflow

Transparent Proxy
A transparent proxy is an Inline proxy. All the connections are intercepted without configuring the host proxy settings. When a server proxy intercepts, connections between hosts and the internet are called transparent. A good example of this is the Fortigate firewall. The firewall has two choices in its security policy properties. You can either have flow-based = Transparent mode or proxy-based = SSL-MODE. The purpose of having a transparent proxy is to make their employees believe they’re not using one. As I mentioned, no configuration is needed on the user’s computer. Also, they’re susceptible to certain security threats, such as SYN-flood DDoS.
Transparent Proxy Workflow

Anonymous Proxy
As the name says, this proxy is all about anonymity. It allows you to do activities on the internet untraceable. An example of this is having a tool like Tor Browser, Firefox, FreeProxy, etc. The anonymous proxy acts the same as the forward proxy. You send your request to a proxy server outside of your organization. The proxy server submits your request. Your source Ip will only be seen by the proxy server and not your requested destination. That means nobody will be able to see your real IP.
Anonymous Proxy Workflow

High Anonymity Proxy
The are three types of proxies.
Level 1 proxy: Elite proxy. When your computer is chained to this proxy, the server you are trying to connect doesn’t know your source IP address, nor doesn’t know that your connection was made via proxy. That’s because all the identifiers headers have been stripped off, so they’re not passed along in requests.
Level 2 Proxy: Anonymous proxy. This proxy hides your real IP address from your targeted server. For example, you want to go to amazon.com. Your actual IP will be parked in the proxy server while the proxy requests your petition. Unlike the level 1 proxy, servers are able to see that you’re coming from a level 2 proxy. This is because the level 2 proxy sends some header information about you.
Level 3 Proxy: Transparent proxy. This proxy does not provide anonymity at all. Instead is best suitable for caching.
High Anonymity Workflow

Distorting Proxy
Distorting proxy is more like hiding your location on the internet. It gives a false Ip address to the targeted website through the headers. For instance, If I live in New York City, it will make it look like I live in San Diego, CA.
Residential proxy
This proxy contains a real IP address provided by your service provider. They are attached to physicals location across the country, state, or city level. It can be expensive. They’re also well-suited for users who need to verify the ads that go on their website, so you can block cookies, questionable or unwanted ads from competitors or bad actors.
Reverse proxy
Unlike a forward proxy, this proxy acts the other way around. Its role is to intercept client requests on behalf of the servers behind it. Upon intercepting those requests, a reverse proxy sends them to the origin server and receives a response from it. Ultimately, its job is to ensure no client communicates directly with the servers.
This proxy is placed in front of web servers and forwards the requests from a browser to the web servers. A good example would be having an F5 appliance at the edge. A reverse proxy makes sense when multiple websites and you do not want direct communications. Also, it could be use to load balance between the servers.
Reverse Proxy Workflow

SSL Forward Proxy
SSL proxy provides decryption between the client and the server. Data is encrypted in both directions. This proxy type is best suited when an organization seeks to enhance protection against threats. To put it in perspective, you encrypt and decrypt traffic based on categories and applications. This type of proxy gives you more visibility for URLs, DNS, Threats, and more.
Imagine you are visiting a secure website. The website contains malicious data/traffic embedded. You try downloading a contaminated file, but the proxy intercepts it and inspects the packet before it gets downloaded to your host. If the proxy sees an anomaly, traffic will be reset/denied or dropped depending on the security aspect.
The only downside of this cool feature is that content cannot be cached, so when you visit websites more than once, you may experience slower performance than you would.
SSL-Forward Proxy Workflow