What is a DNS Proxy:
It’s a forward proxy and acts like any other regular proxy. It sits in the middle of your network and forwards requests and replies between DNS clients and servers. Imagine you are sitting in your workstation, and you query www.amazon.com. Without a proxy, traffic will be sent to your local DNS server. If your local DNS doesn’t know how to get to amazon, it will use the DNS forwarders to send it out to the public DNS servers.
What is the purpose of a DNS Proxy:
A DNS proxy simplifies network management, plain and simple.
In perspective, every time you change your DNS servers, you will have to rework all the DNS settings in all your devices. Having a DNS proxy in place allows us to make changes in one place only. For instance, let’s imagine you have two local DNS servers and need to change the IP address for some reason. All the new DNS updates will be made in the proxy rather than going to each client. You will update the proxy with the new server IP addresses.
When do I need a DNS proxy?
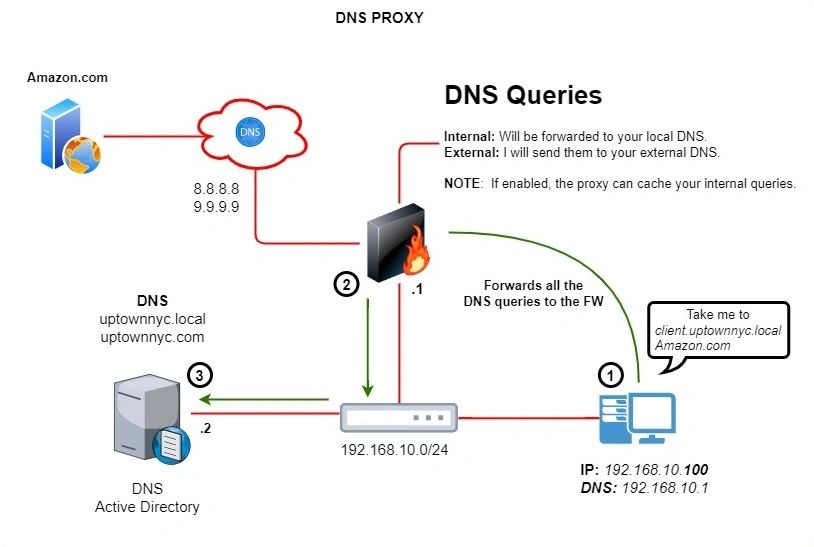
In my experience, this is very useful in medium and enterprise organizations. I will tell you why. Imagine you have an HQ and three branches. It wouldn’t make sense to install a DNS server at each site, right? Instead, we can point all the clients to your DNS proxy. Ideally, you want to send all the internal queries to your HQ local DNS and everything else to the public 8.8.8.8 and 9.9.9.9.
How to configure a DNS Proxy Using Palo Alto Firewalls
Pre-requisites
– Basic knowledge of the firewall is needed.
– The firewall needs to be reachable.
– The IP default gateway will be used as a proxy.
– The clients will use the firewall default gateway IP as a DNS.
– The firewall proxy will have the local DNS added and local domains.
Diagram:

Step1:
Login to your Palo Alto firewall and click on the network tab. Then, on the left panel, click on DNS Proxy. At the bottom, click on (+Add).
- Check the enable box.
- Add a name.
- Add the primary and secondary external DNS servers.
- Add the interface that acts as a default network for your clients. NOTE (if your default gateway is NOT in the firewall but instead on the switch, then you need to put whatever is on the firewall acting as a transit default gateway).
DNS Proxy rules
The proxy rules allow you to specify domain names corresponding to your primary and secondary DNS servers. For example, if you want to go to your local DNS server at domain.mycompany.local or related, you need to add these entries for you to query them. If there’s no match, the firewall can drop it or send it to the external DNS servers.
- Click on add.
- Add a name and enable caching if needed. (Recommended)
- Start adding all your local domain names using wildcards to cover the whole plane.
- At the bottom, add Your primary and secondary DNS servers.
- Click OK.

Static Entries
This option allows you to configure static FQDNs to IP mappings. For instance, let’s imagine you have a wireless portal or splash portal for your guests. You want them to agree to your conditions before they get access to your Wi-Fi. When devices get a DNS address, any device that queries wirelessportal.uptownnyc.local will be forwarded to the static IP address that the firewall is giving you.

After adding all the necessary configurations, click OK. And then commit the changes on the Palo.
Step2:
Configuring the client DNS.

Step3:
How to verify if the proxy works.
Ping any domain name or visit any internal website that allows you to query your DNS.
For example, I will ping client.uptownnyc.local and wirelessportal.uptownnyc.local.
Login to Palo CLI using putty or some sort.
Run this command for verification – “show dns-proxy cache all”
Run this command if you want to clear your cache – “clear dns-proxy cache all”
NOTE: If you see no entries on your verification is because you haven’t queried your internal DNS network.

Another useful command is to run – “show session all filter application dns-base”
This command allows viewing when a host does a nslookup to any domain. You’ll see their sessions telling you the proxy is working fine.